Technology
Auracast: The Future of Bluetooth Technology for Wireless Audio
Bluetooth technology has revolutionized the way we connect wireless devices, particularly in the realm of headphones and headsets connecting to computers and smartphones. However, this technology is constantly evolving, with the next version poised to function much like a Wi-Fi....
Samsung Exynos 2400 with Satellite Communication and 70% Faster Performance
Samsung has officially unveiled its latest flagship processor, the Exynos 2400. This powerful new SoC (System on Chip) is set to revolutionize mobile gaming and satellite communication, with a strong possibility of making its debut in the highly anticipated Galaxy....
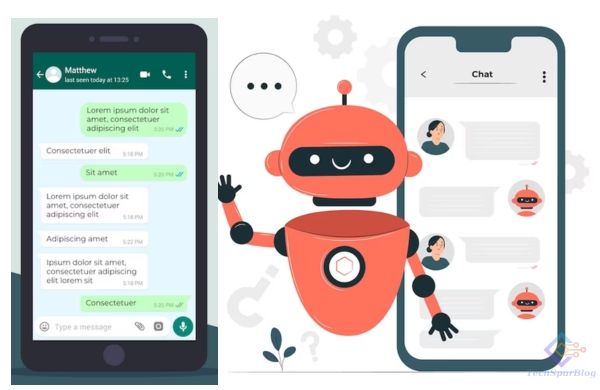
WhatsApp Introduces Meta AI Chatbot to Enhance User Experience
In a move that promises to revolutionize the messaging landscape, Meta, the parent company behind WhatsApp, Instagram, and Facebook, has announced the integration of its Meta AI chatbot into WhatsApp. This exciting development was unveiled during Meta Connect 2023, with....
Modern Outlook Experience: New Logo and Animations for Windows Users
Microsoft has made a significant announcement that has garnered the attention of Windows users worldwide. The tech giant has unveiled the new Outlook for Windows, making it generally available for personal accounts through the Microsoft Store on Windows 10 and....
MIT’s Innovative Robotic Research: Teaching Machines to Handle Objects More Human-Like
While robotic innovation continues to advance rapidly, robots still have much to learn from humans when it comes to object manipulation. A recent study conducted at the Massachusetts Institute of Technology (MIT) has proposed an innovative method to teach machines....
How to Use Check In on iOS 17 to Keep Loved Ones Informed
In our fast-paced world, staying connected with loved ones is more critical than ever. Fortunately, iOS 17 introduces an innovative feature called “Check In,” designed to help you effortlessly share your location and well-being with friends and family. Whether you’re....
FaceTime on Apple TV 4K with TVOS 17
This new feature allows you to transform your video calls into larger-than-life experiences, bringing your loved ones closer to you on the big screen. Here we are explain you through the steps of using FaceTime on Apple TV 4K and....
How to Be Tech-Savvy: A Comprehensive Guide to Safeguarding Your Digital World
In today’s technologically advanced society, it’s crucial to be not just digitally literate but also tech-savvy. Being tech-savvy means you can efficiently and safely navigate the vast digital realm, recognizing potential threats and capitalizing on opportunities. This encompasses a broad....
The Top 9 Ways Businesses Can Benefit from iPaaS
The digital world we live in today is incredibly complex – there are so many different technologies, data sources, and software programs in all directions. While all this connectivity has opened up tremendous opportunities, it feels overwhelming to integrate everything and....
The Emergence of AI Writing Tools: Revolutionizing Content Creation
In the current digital landscape, AI writing tools have risen as invaluable allies for content creators. These tools, driven by sophisticated algorithms and machine learning, are transforming how we approach writing, making it more efficient and accessible. This article delves....