Cloud-powered innovation moves fast, but breaches erode customer trust slowly. With data and apps increasingly centralized on Azure, a startling majority of security executives report lacking confidence in ensuring workloads remain secured reliably post-migration while delivering at DevOps speeds.
This presents an urgent paradox – how to accelerate securely?
The answer lies in embracing automation philosophies end-to-end, beyond enabling velocity but more crucially consistent guardrails safeguarding compliance and best practice hygiene at the enterprise scale.
Read on to guide your Azure journey balancing uncontrolled creativity with customer confidence.
Centralizing Identity Lifecycle Governance
Securing identities accessing cloud resources proves foundational before provisioning infrastructure or working with data.
Azure Active Directory (AAD) delivers robust access governance across hybrid/multi-cloud environments including:
-
Strict access policies enforcing MFA, and and sign-in risk checks before granting access
-
Privileged identity management workflows for just-in-time admin elevation
-
Access reviews to re-certify user access appropriateness quarterly
-
Lifecycle management automating access revocation when staff switch roles
Additionally, AAD External Identities facilitates securely collaborating with partners by granting limited access to cloud resources. Auditing all access attempts ensures compliance.
Also Read: Everything You Need to Know about DevOps Automation
Instituting Infrastructure Compliance Guardrails
Governing cloud resources at scale is crucial before deploying any workloads. Azure Policy Initiatives offers a a cloud governance blueprint helping balance compliance with developer agility including:
-
100+ built-in policy definitions ensuring compliance with regulatory standards like SOC2, ISO27001, HIPAA
-
Initiative Bundles customize guardrail templates meeting unique organizational requirements
-
Remediation tasks scan existing resources flag deviations from policy fix inconsistencies at scale
-
Effect metadata allows setting policies to audit-only or enforce mode proportionate to risk priority
Equally powerful, Azure Security Center continually monitors configurations by applying AI-based threat detection to identify anomalies. Any governance drifts get auto-flagged for remediation upholding hygiene.
Embed Security in CI/CD Pipelines Workflows
Migrating apps to the cloud requires rebuilding delivery pipelines integrating security, compliance and testing consistently across the lifecycle.
Azure DevOps Services helps embed controls natively across pipelines workflows comprising:
-
Static code analysis identifying vulnerabilities early even before new code gets committed
-
Dynamic security testing later in pipeline scans compiled code for risks before promotion to higher staging environments
-
Infrastructure compliance checking as final automated gating validating security configurations remains intact on running systems right before production deployment approvals
Together, this structured sequence weaves preventative security governance into engineering rhythms achieving frictionless ubiquity and verifying defenses remain intact throughout rapid enhancements. Shift security left through pipelines!
Also Read: Top Automation Testing Tools for Software Performance
Immutable Infrastructure to Restrict Attack Surfaces
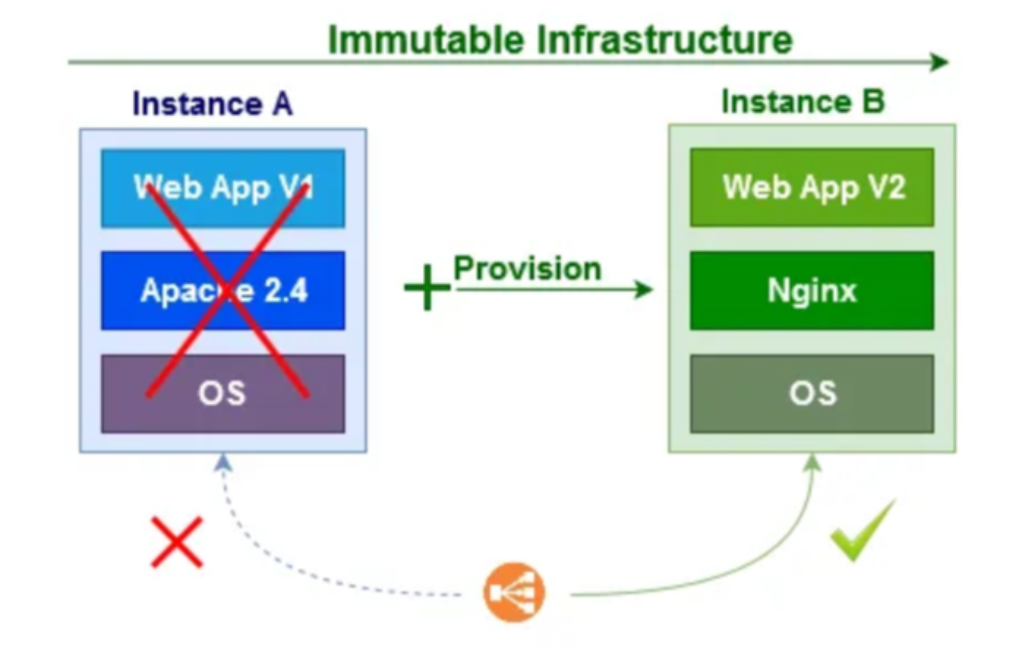
Azure virtual machine templates allow provisioning infrastructure securely as read-only immutable gold images resisting adversarial changes post-deployment. Benefits include:
-
Hardened platform configurations persisting reliably containing attacker dwell times
-
Malware degraded to only access compute not customize persistence
-
Control plane integrity checking resources haven’t diverged from the desired baseline
-
Rapid rebuilds easily restore compromised build consistency in minutes
Pairing hardened gold images with continuous compliance monitoring minimizes threat surfaces that emerge through infrastructure drift or temporary lapses of vigilance while empowering rapid rebuild.
Safeguarding Sensitive Data via Classification and Encryption
Innovation demands accessing sensitive data – be it customer PII, financial records or proprietary IP.
While Azure data security delivers robust encryption controls protecting data assets at rest and in transit, classifying and labelling sensitivity consistently remains imperative in managing permissions.
Effectively balancing access needs with responsible data handling minimizing breach risks.
Azure Information Protection provides unified data classification, labeling and protection tooling applying appropriate controls as data traverses across services.
Automated or manual sensitivity labelling embeds metadata persisting visibility even when files get copied across endpoints or shared externally.
Usage conditions configure permissions, encryption requirements and access restrictions proportionate to sensitivity grades.
For example, highly confidential data requires multi-factor authentication and time-restricted access only on managed devices.
While moderate sensitivity assets mandate encrypted transmission via HTTPS but allow broader information worker access meeting daily productivity needs.
Together data visibility and adaptive protections prevent oversharing risks.
Adopting DevSecOps to Democratize Security
Weaving preventative security strategically across pipelines promises to institute safeguards reliably at enterprise scale yet checkpoint gating risks teams side-stepping controls chasing expediency temporarily reaping fool’s bargain short term.
Mature DevSecOps culture overcomes such antipatterns through democratizing security equitably.
DevSecOps succeeds in sustaining secure velocity by creating shared accountability between builders seeking innovative possibilities and stewards of custodians’ responsible outcomes.
Through empathy, influence and incentives polarities dissolve into participating pluralism holding all contributors collectively responsible for shipping high-quality and trustworthy systems.
Some leading signals that characterize transformation well underway include security teams consulted early in requirements.
Also Read: Building Serverless SharePoint Solutions with Azure Logic Apps
Activating Zero Trust for Stronger Defenses
The shift to more digital technology means people now access apps and data from many devices and networks.
This raises the importance of “zero trust” security to persistently confirm access.
Azure Active Directory Conditional Access rules strengthen sign-in protection through adaptive safeguards checking user ID, device safety, app sensitivity, and sign-in risk levels before granting entry. This minimizes infiltration risks from all angles.
Key uses of zero trust advanced by Azure include:
-
Employees working remotely must use approved devices and geo-fenced locations before accessing apps
-
Sensitive financial data necessitates heightened defences against suspicious login attempts
-
Blocking outdated authentication closes security holes that allow adversaries to sneakily steal credentials offline
Growing Globally Diverse Cybersecurity Talent
Longtime cybersecurity skill shortages worsen risks amid rising job openings outpacing hiring rates.
Equally harmful, concentrating talent in limited regions magnifies critical expertise gaps further with disconnected specialization silos between interrelated cyber fields.
Progress requires diversifying talent pipelines worldwide unlocking overlooked communities enduring unfair obstacles, especially impacting minority groups and developing regions historically denied equal opportunities to secure technology universally accessed.
Steps forward include:
-
Offering secure coding instruction expanding career on-ramps
-
Valuing neurodiversity which contributes to specialized strengths
-
Demystifying expertise via wide access to preparatory mentoring
Spreading cyber defense globally advances possibilities while elevating historically disadvantaged communities ultimately strengthening collective resilience.
Enforcing Least Privileged Access Strictly
Generous access greases productivity short term yet proves disastrous longer term once compromised credentials unleash data breaches and ransomware laterally infiltrating across entire estates.
Azure AD Privileged Identity Management (PIM) enforces the least privileges minimizing standing access while securely elevating permissions just in time
PIM discovers standing privileged roles across Azure AD, Azure platform, Office 365 and Dynamics 365 assets providing time-limited access only upon approval workflows.
Authorization duration gets configured down to minutes with automatic revocation post expiry terminating sessions sharply minimizing adversary dwell time likelihood.
Equally crucial, PIM activation alerts trigger incident response playbooks the moment suspicious security events indicate potential identity compromise attempts containing breaches early before escalation.
Architect least privilege access strictly assuming breach probability taming dangers through robust identity hygiene.
Also Read: How to Host a Static Website in Azure Cloud for Free
Actioning Threat Intelligence with Microsoft Defender
Guarding huge, ever-changing cloud systems requires tapping AI-powered threat clues to spot sophisticated, stealthy cyber attacks obscuring initial reconnaissance and patiently hiding before striking key targets quietly.
Microsoft Defender for Cloud uniquely combines Microsoft’s global threat research surpassing any single organization’s visibility with swift, automated playbooks accelerating coordinated security responses across the whole enterprise.
Alerts trigger unusual signals like suspicious login locations, unlikely travel, odd access timing, or suspicious IP addresses suggesting threats lurking unseen.
Expert systems analyze interrelated events to discern hard-to-spot attack patterns across fragmented signals like reconnaissance movements or internal data probing connecting the dots.
Playbooks codify incident response procedures to standardize security workflows, sanitize affected assets, and methodically enact hunting and prevention controls.
Together, Defender for Cloud custom-fits global insights using each organization’s cloud signals that individuals often miss to spot threats early.
This unified command of collective insights promises formidable protection while keeping transparency risks in check!
Balancing cloud security and DevOps speed seems daunting yet Azure offers a prescriptive blueprint intrinsically embedding security natively into code flows to customers.
Core priorities include centralizing identity governance, enabling policy guardrails codifying compliance requirements, and shifting security safeguards left applying controls natively through pipelines.
Become a multiplicative force upholding trust!
Let us promote an empowered yet responsible innovation culture balancing creativity with consistent security guardrails built by design.
How will you drive secure transformation within your Azure journey? Let us know in the comments below

Techspurblog is a blog dedicated to providing industry-leading insights, tips, tricks and tools on topics such as web design, app development, Digital Marketing, Education, Business and more. We also provide reviews of the latest tech products and services that can help you get the most out of your business.






